JUNOS_BGP Flowspec
BGP FlowSpecの検証
構成は↓
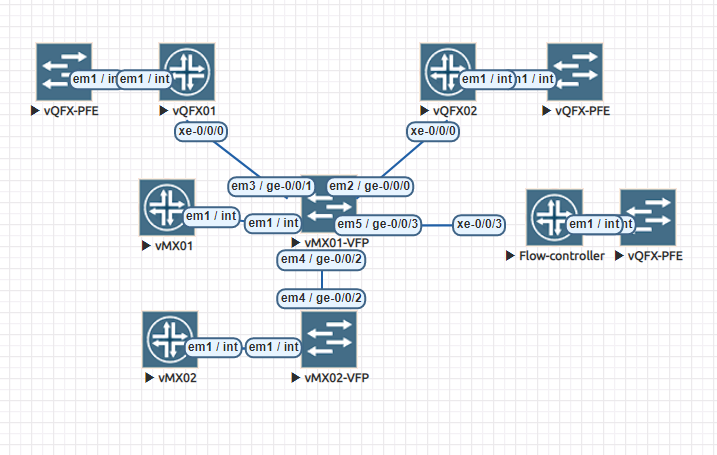
今回は
vQFX01/02をキャリア(ISP)と仮定して、そこから自社内への通信をFlowSpecで制御してみる。
vQFX01
set interfaces xe-0/0/0 unit 0 family inet address 1.1.1.0/31
set interfaces em1 unit 0 family inet address 169.254.0.2/24
set interfaces lo0 unit 0 family inet address 100.100.100.1/24
set interfaces lo0 unit 0 family inet address 100.100.200.1/24
set routing-options autonomous-system 1
set protocols bgp group EXT type external
set protocols bgp group EXT export LOOPBACK
set protocols bgp group EXT neighbor 1.1.1.1 peer-as 3
set protocols igmp-snooping vlan default
set policy-options policy-statement LOOPBACK from protocol direct
set policy-options policy-statement LOOPBACK then accept
vQFX02
set interfaces xe-0/0/0 unit 0 family inet address 2.2.2.0/31
set interfaces em1 unit 0 family inet address 169.254.0.2/24
set interfaces lo0 unit 0 family inet address 200.200.200.1/24
set interfaces lo0 unit 0 family inet address 200.200.100.1/24
set routing-options autonomous-system 2
set protocols bgp group EXT type external
set protocols bgp group EXT export LOOPBACK
set protocols bgp group EXT neighbor 2.2.2.1 peer-as 3
set protocols igmp-snooping vlan default
set policy-options policy-statement LOOPBACK from protocol direct
set policy-options policy-statement LOOPBACK then accept
vMX01
set interfaces ge-0/0/0 unit 0 family inet address 2.2.2.1/31
set interfaces ge-0/0/1 unit 0 family inet address 1.1.1.1/31
set interfaces ge-0/0/2 unit 0 family inet address 10.1.1.0/31
set interfaces ge-0/0/3 unit 0 family inet address 172.16.1.0/31
set routing-options static route 192.168.1.0/24 next-hop 10.1.1.1
set routing-options flow term-order standard
set routing-options autonomous-system 3
set protocols bgp group EXT type external
set protocols bgp group EXT export STATIC
set protocols bgp group EXT neighbor 1.1.1.0 peer-as 1
set protocols bgp group EXT neighbor 2.2.2.0 peer-as 2
set protocols bgp group INT type internal
set protocols bgp group INT neighbor 172.16.1.1 family inet flow
set protocols bgp group INT neighbor 172.16.1.1 peer-as 3
set policy-options policy-statement STATIC term 10 from protocol static
set policy-options policy-statement STATIC term 10 then accept
set policy-options policy-statement STATIC term 20 from protocol bgp
set policy-options policy-statement STATIC term 20 from external
set policy-options policy-statement STATIC term 20 then reject
vMX02
set interfaces ge-0/0/2 unit 0 family inet address 10.1.1.1/31
set interfaces lo0 unit 0 family inet address 192.168.1.1/32
set interfaces lo0 unit 0 family inet address 192.168.1.2/32
set interfaces lo0 unit 0 family inet address 192.168.1.3/32
set routing-options static route 0.0.0.0/0 next-hop 10.1.1.0
Flow-controller
set interfaces xe-0/0/3 unit 0 family inet address 172.16.1.1/31
set interfaces em1 unit 0 family inet address 169.254.0.2/24
set forwarding-options storm-control-profiles default all
set routing-options autonomous-system 3
set protocols bgp group INT type internal
set protocols bgp group INT neighbor 172.16.1.0 family inet flow
set protocols bgp group INT neighbor 172.16.1.0 peer-as 3
BGP FlowSpecに関係したConfigは青字部分
今回は、Flow-controllerもJUNOSで代用
まず、この状態で、vQFX01からPing/Tracerouteを実施
root@vQFX01# run ping 192.168.1.1 source 100.100.100.1
PING 192.168.1.1 (192.168.1.1): 56 data bytes
64 bytes from 192.168.1.1: icmp_seq=0 ttl=63 time=107.916 ms
64 bytes from 192.168.1.1: icmp_seq=1 ttl=63 time=101.950 ms
64 bytes from 192.168.1.1: icmp_seq=2 ttl=63 time=102.052 ms
64 bytes from 192.168.1.1: icmp_seq=3 ttl=63 time=102.030 ms
64 bytes from 192.168.1.1: icmp_seq=4 ttl=63 time=102.719 ms
^C
--- 192.168.1.1 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max/stddev = 101.950/103.333/107.916/2.308 ms{master:0}[edit]
root@vQFX01#{master:0}[edit]
root@vQFX01# run traceroute 192.168.1.1 source 100.100.100.1
traceroute to 192.168.1.1 (192.168.1.1) from 100.100.100.1, 30 hops max, 40 byte packets
1 1.1.1.1 (1.1.1.1) 103.948 ms 198.099 ms 199.793 ms
2 192.168.1.1 (192.168.1.1) 199.716 ms 199.000 ms 199.334 ms{master:0}[edit]
root@vQFX01#
問題なし。 勿論、Sourceを「100.100.200.1」に変えても同様。
では、Flow-controllerに以下の設定を入れる
set routing-options flow route FLOWSPEC match protocol icmp
set routing-options flow route FLOWSPEC match destination 192.168.1.1/32
set routing-options flow route FLOWSPEC match source 100.100.100.1/32
set routing-options flow route FLOWSPEC match icmp-type echo-request
set routing-options flow route FLOWSPEC then discard
要はACLで言うところの以下の ルール
Source:100.100.100.1
Dest:192.168.1.1/32
Protocol:ICMP Echo
Action:Discard
では、再度確認
root@vQFX01# run ping 192.168.1.1 source 100.100.100.1
PING 192.168.1.1 (192.168.1.1): 56 data bytes
^C
--- 192.168.1.1 ping statistics ---
8 packets transmitted, 0 packets received, 100% packet loss{master:0}[edit]
root@vQFX01#
→Pingはダメ
root@vQFX01# run traceroute 192.168.1.1 source 100.100.100.1
traceroute to 192.168.1.1 (192.168.1.1) from 100.100.100.1, 30 hops max, 40 byte packets
1 1.1.1.1 (1.1.1.1) 102.277 ms 198.594 ms 199.724 ms
2 192.168.1.1 (192.168.1.1) 202.355 ms 198.665 ms 200.243 ms{master:0}[edit]
root@vQFX01#
→TracerouteはOK
ちなみに・・・vMX02から100.100.100.1 へのPingは・・・
root@vMX02# run ping 100.100.100.1 source 192.168.1.1
PING 100.100.100.1 (100.100.100.1): 56 data bytes
64 bytes from 100.100.100.1: icmp_seq=0 ttl=63 time=104.504 ms
64 bytes from 100.100.100.1: icmp_seq=1 ttl=63 time=102.707 ms
64 bytes from 100.100.100.1: icmp_seq=2 ttl=63 time=102.930 ms
64 bytes from 100.100.100.1: icmp_seq=3 ttl=63 time=173.753 ms
64 bytes from 100.100.100.1: icmp_seq=4 ttl=63 time=104.565 ms
64 bytes from 100.100.100.1: icmp_seq=5 ttl=63 time=103.756 ms
64 bytes from 100.100.100.1: icmp_seq=6 ttl=63 time=103.439 ms
64 bytes from 100.100.100.1: icmp_seq=7 ttl=63 time=103.366 ms
^C
--- 100.100.100.1 ping statistics ---
8 packets transmitted, 8 packets received, 0% packet loss
round-trip min/avg/max/stddev = 102.707/112.377/173.753/23.206 ms
問題なし。
では、vMX01のrouting tableをcontroller前後で確認
変更前
root@vMX01# run show route protocol bgp
inet.0: 14 destinations, 17 routes (14 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both1.1.1.0/31 [BGP/170] 00:37:47, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
2.2.2.0/31 [BGP/170] 00:37:14, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0
100.100.100.0/24 *[BGP/170] 00:37:47, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
100.100.200.0/24 *[BGP/170] 00:37:47, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
169.254.0.0/24 *[BGP/170] 00:37:47, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
[BGP/170] 00:37:14, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0
200.200.100.0/24 *[BGP/170] 00:37:14, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0
200.200.200.0/24 *[BGP/170] 00:37:14, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
変更後
root@vMX01# run show route protocol bgp
inet.0: 14 destinations, 17 routes (14 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
]
1.1.1.0/31 [BGP/170] 00:39:01, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
2.2.2.0/31 [BGP/170] 00:38:28, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0
100.100.100.0/24 *[BGP/170] 00:39:01, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
100.100.200.0/24 *[BGP/170] 00:39:01, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
169.254.0.0/24 *[BGP/170] 00:39:01, localpref 100
AS path: 1 I, validation-state: unverified
> to 1.1.1.0 via ge-0/0/1.0
[BGP/170] 00:38:28, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0
200.200.100.0/24 *[BGP/170] 00:38:28, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0
200.200.200.0/24 *[BGP/170] 00:38:28, localpref 100
AS path: 2 I, validation-state: unverified
> to 2.2.2.0 via ge-0/0/0.0inet6.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
inetflow.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both192.168.1.1,100.100.100.1,proto=1/term:1
*[BGP/170] 00:00:09, localpref 100, from 172.16.1.1
AS path: I, validation-state: unverified
Fictitious
新しく「inetflow.0」というtableが出現している。
ネットで調べれば細かい情報が出ているので、一旦はこれで終わり。
今回はFlowspecの機能復習がメインで、JUNOSをControllerとして代用したけど、NetFlow等でフローを採取できる仕組みが必要。
なお、DDoS対策的な機能としては、BGP FlowSpec以外にもRTBH等の技術もあるけど、細かい制御はFlowSpecの方が優れている・・・というか、RTBHを先にやるべきだったなぁ・・・
検証はしたものの、実務においては回線費用が従量課金が殆どだと思うので、実際にはトラフィックがvMX01まで来てしまったら、微妙じゃね?というイメージ。
ただ、キャリアのこういうサービスは別料金が基本だろうからやらないよりはやった方がいいのは間違いない。